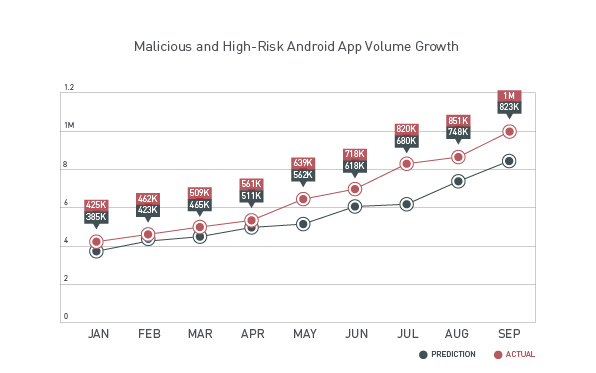
With increasing usage of Google Inc. (NASDAQ:GOOG) owned Android and Apple Inc.’s (NASDAQ:AAPL) iOS powered Smartphones, the number of malware threats and high risk apps have seen a significant growth. Cyber criminals are making constant efforts to develop efficient and undetectable malware apps which can steal sensitive personal data. Earlier in Q2, the Android volume threat grew and had reached 718,000 by June 2013, according to Trend micro. Recently, the figure surpassed the 1 million mark, alarming a majority of Smartphone users to remain extra cautious and avoid hazards.
Malicious & High Risk Apps Recorded A 39.2% Increment Compared To The Last Quarter!
If we analyze the graph below, the volume of threats is continuously on the rise at an explosive rate on a monthly basis and the increment is much higher than the predicted value. Earlier in January 2013, the volume of malicious and high risk apps was around 425,000 and it almost doubled in the next 6 months (June), reaching the 718,000 mark. In the second half of 2013, the figure saw a steady increase from 718,000 in June to 820,000 in July, then 861,000 in August and finally surpassed the 1 million mark in September 2013. Compared to Q2, an increment of 39.2% was registered in the volume of risky and malicious apps.
Nearly 4 in 5, that is 80% of high risk apps performed malicious routines, while the remaining 20% had a high risk routine like that of an adware. Hackers are successfully cashing in on the vulnerabilities in the Android and iOS devices and are duping mobile device users across the globe. In Q3 alone the Smartphone shipment rose to 250 million in sales. This figure is indeed motivating for hackers worldwide. Users are often tricked in and end up disclosing personal details which are used by hackers to perform banking transactions or to trick other friends of the victimized users on various social media platforms by posting spam on the users’ behalf. Nearly 15% of social media reviews are expected to be fake.
Amongst the malware and risky apps, info-stealing FAKEINST took the top spot, accounting for 34% of malicious threats followed by malware-downloading OPFAKE (30%). OPFAKE comes bundled along with the well-known mobile browser Opera Mini. FAKEINST is yet another Android malware program which has proved dangerous for users. Both of these are known to target Android phones and steal money or bounce cash to other accounts by sending SMS messages without the user’s knowledge to a premium rate number and collect data about the victimized device. Personal data related bank accounts or social media profile login details are likely to cause nightmare for victims. In 2012, nearly $4.9 billion were stolen from the consumer banking accounts through malware attacks.
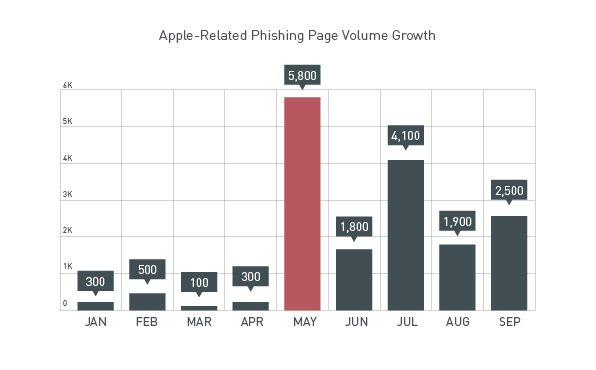
Apple Inc. (AAPL)’s iOS Was The Top Choice For Mobile Phishing, Leading To Identity Thefts!
Apple was one of the top phishing targets for cyber criminals across the globe. The volume growth in Apple related phishing sites reached 8,500, an increase of 8.9% from 7,800 in the previous quarter, and a whopping 844% increase compared to the first quarter figures of 900. There was a sudden spike in mobile phishing sites in May due to rumors about the iOS 7 release. In June and July, news about the iPhone 5c was floating in the market, providing a mouth-watering opportunity for hackers, resulting in yet another spike in growth of phishing sites.
Innovations like the Apple Touch ID finger print sensor might bring some relief to the users in their efforts to try and remember different passwords for different accounts, but it is likely to provide a gateway to hackers in innovating new and undesirable malware threats and cause serious damages for users. Touch ID was the main target in the recent past, due to its use as a key controller for multiple Apple products. Mobile phishing sites targeting users across various Apple products are asking for their government IDs. These could be used for identity thefts. The hackers have gone a step ahead from asking the usual email id, password & bank details and moved on to Government ID to successfully utilize the same for identity thefts.
Source: Trend Micro