The email accounts of numerous C-level executives around the world have been compromised and a threat actor is now selling their credentials online!
According to recently surfaced news, the data is currently being sold in a restricted underground forum for Russian hacked called ‘Exploit.in’. The username and password combinations for the executives are for Office 365 and Microsoft accounts which according to the hacker belong to executives at roles such as CEO, COO, CFO, CTO, President, Vice President and so on.

The access to email account of each executive is sold for $100 to $1500, depending on the company size and employee’s role.
But, are these accounts legit?
Yes, they are! A source from the cyber-security community contacted the seller to obtain samples and verified the legitimacy of the threat actor’s claims. The source collected credentials for two accounts, one belonging to the CEO of a U.S medium-sized business and another which belonged to the CFO of an EU-based multi-chain retail outlet. Both of them turned out to be valid.
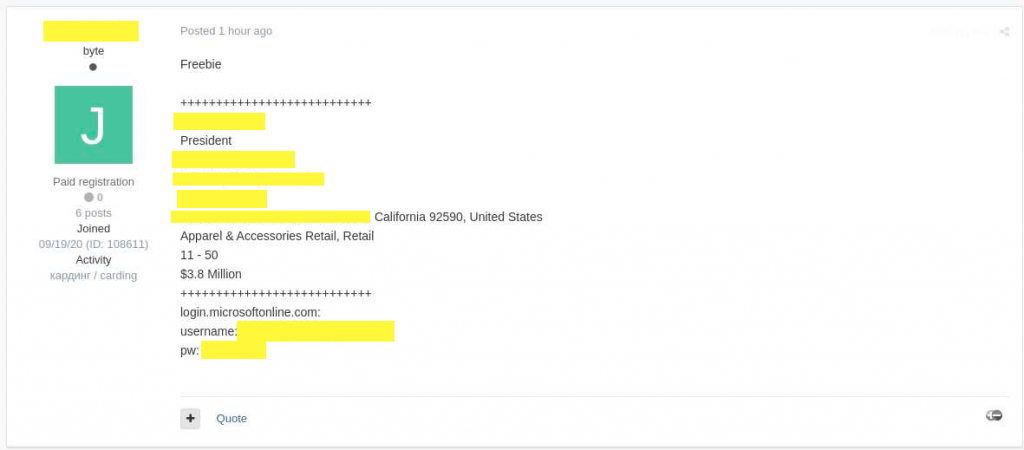
The source who requested not to be named also mentioned that the seller refused to answer when asked how did he obtain the login credentials but in turn said that he had many more to sell in the near future as well.
KELA which is a threat intelligence firm, taking note of this incident reported that the same threat actor had previously shown his interest in buying “Azor logs” which refers to data collected from devices infected with the trojan called “AzonUlt infostealer”.
An infostealer trojan is a notorious malware which logs usernames and passwords from browsers that are infected with it. Later on, the operator who had deployed the infostealer filters, organizes the data and puts it up for sale in various hacking forums.
According to Raveed Laed who is KELA’s Product Manager, this particular hack of corporate email credentials is highly valuable for cybercriminals as there exist number ways in which they can monetize them.
For instance, a cyber attacker armed with this data can use the internal communication of a company and pull of a ‘CEO scam’ wherein they ask employees to wire them large sums of money. This data can also be used by cybercriminal to access other even more sensitive information which can later become a part of an extortion scheme. Or, alternatively, the compromised credentials can also be used to bypass email-based 2FA after which a hacker can conduct a network intrusion.
The recent incident of Twitter hacking is a great example of how hackers can misuse the accounts of who’s who of the industry. Accounts of Elon Musk, Jeff Bezos were used to putting out a tweet asking users to send money to a particular account.
But, nonetheless, it is being predicted that the email login details will mostly be used only in ‘CEO scams’, also known as BEC scams. Why so? Because a report by the FBI indicated that BEC scams were far the most popular form cyber attack in 2019 which accounted for half of all monetary losses in cybercrime.
So, what exactly can you do to prevent falling prey to attackers who steal your login details in the first place? The easiest way is to set up two-step verification (2SV) or two-factor authentication aka 2FA solution.
By doing this, even if hackers somehow manage to steal your login details, it will be pretty much useless as it would need an additional 2SA or 2FA verifier. We will keep you updated on all future developments. Until then, stay tuned.

