Are you an Android user and missing some of the much-needed security features that iOS 14 users have been enjoying now? You must pay attention to it.
Data privacy has become a sweeping concern for all gadget users in this day and age. Ever since the inception of mobile communication devices and the internet, user trust has been breached with revelations of surveillance, spyware, and malware.
As technology has advanced, it has become even defter in its ability to be used as a weapon against user privacy, losing a large part of its convenient appeal in the process. This is not to say that most living people today do not use technology at all, but this usage comes with an associated sense of helplessness and paranoia about the troves of information, we now know for sure, different technological services collect.
Mics and cameras are one such area of massive paranoia, and understandably so, as features specifically built to record images and audio feel inherently invasive, regardless of whether their usage is controlled or not.
Over the years, fears of being spied upon by our IoT devices’ webcams and microphones have mounted, and even been confirmed in various cases. Instances of eerily precise targeted advertisements have led many users to believe that their phones are recording their conversations and using them as intel.
Up until mid-2020, not even a single mobile OS offered a direct security feature against such breaches, until Apple introduced a range of new security features with iOS 14 for all iPhone and iPad users.
One of the most notable features of the new iOS 14 is the “access dot”. With this, users get a different coloured dot above their phone’s notification bar when the mic or camera is being used by an app. The dot is green for camera alerts and orange for mic alerts. Furthermore, users can also check the concerned application, time of use, and duration of use in their phone’s control centre.
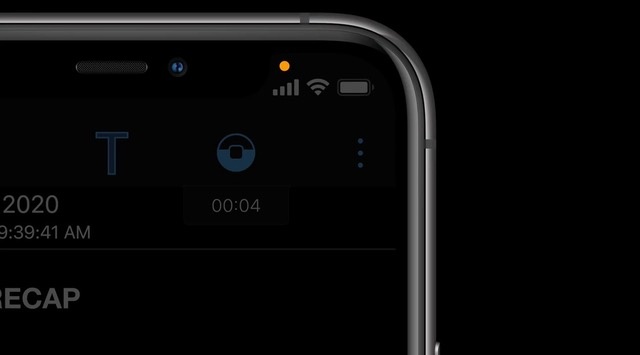
Naturally, then, this might seem like yet another in-built security feature Android users are missing out on. It’s true to a certain extent as Google and other OEMs have not given much heed to users’ requirements and requests. But this is noticed by an independent app developer whose app is turning heads.
Access Dots: Replicating iPhone Security Experience
“Access Dots” is an app by an XDA developer jagan2, which performs the same functions as iPhone’s dot alerts, but on the Android OS.
The app needs to be downloaded from the Google Play Store, unlike the in-built version in iOS. it is a third-party app.
The app has two versions, one which is free and performs all basic functions, and one which can be purchased by making a donation of $2.00 (RS 170), with more customization options.
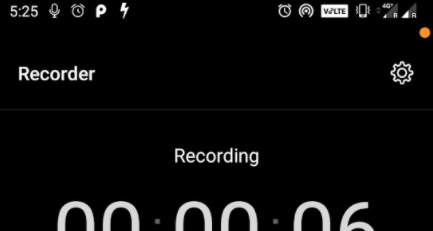
The Android app needs access to the device’s activity in order to activate, and once it has been activated, it alerts the user whenever the camera or mic is being used – something that iOS 14 users are finding much needed. But the developer of Android Dots app has taken it to a whole new level.
The default colour configurations for the Access Dots are the same as iOS, green for the camera, and orange for the mic, but these can be changed if one is using the paid version, a feature iOS doesn’t yet offer. Additionally, users can personalize the dots’ sizes and positions in the paid version, selecting dimensions and placements that are most convenient for them.
Access Dots provides a log for all the apps that accessed the camera and mic, along with the time stamp and duration of use.
Being a third-party app, however, Access Dots might raise privacy concerns for some. To gain a deeper understanding of the app’s mechanisms, Davey Winder, a journalist working for Forbes, directly raised these concerns with the developer.
In response to this the developer stated, “regarding the logs, it’s just very specific info about which app was in the foreground at the time of access. This is recorded locally on the device and is not sent anywhere. To be more precise, the app itself doesn’t collect any data whatsoever apart from the logging which is stored locally and displayed only on the Access Log page.”
Thus, considering that the app stores all collected data locally, it is fairly safe to use.
Essential For Security And Privacy
Devices have become vulnerable, and a major portion of this vulnerability can be attributed to permission access and terms and conditions compliance.
User agreements are extremely tedious to read and decipher and a majority of users agree to them without so much as a glance. According to a study conducted late last year, only 1% of technology users read user agreements before agreeing to them.
Similarly, apps sometimes end up having unbridled access to device permissions, ranging from camera and microphones to the device’s gallery, contacts, and text messages because users are often in the habit of granting permissions without reading the type of permission being asked for in the first place.
Thus, a feature like the multicoloured dots of iPhones and Android phones has dual-advantage. On the one hand, it actively alerts users of suspicious activity while providing a detailed log of said activity for further troubleshooting, but at the same time, it also works as an awareness generation feature which will hopefully make users more mindful of permissions and the kinds of apps they keep on their phone in the long-run.
The effects of this feature on tech giants are already being seen, for instance, a lawsuit was recently filed against Facebook when a user received an alert on her iPhone about Instagram’s unauthorized usage of the camera. Facebook brushed this off as a bug, but the case still seems to be ongoing.
The iOS 14 has many other such security-oriented features and with the newly launched Android 11, the security of Android devices is also set to become tighter, with a feature specifically geared towards app permissions.
Are These Security Concerns Justified?
Tech companies constantly try to ensure users of the absolute safety of their data. Building and maintaining trust is one of the foundations of any two-way exchange. Despite these efforts, slip ups often happen.
Back in June, Google Chrome extensions were found to be surveilling users. Earlier this year, when work-from-home had just started coming into effect, a law firm in the UK advised users to keep all home assistants such as Amazon Alexa and Google Voice Assistant switched off during working hours. Additionally, it was confirmed last year that Alexa and Google Home record and listen to users’ activity even when they are supposed to inactive. Google also came under fire for listening to snippets of users’ Skype calls to improve their translation service.
These examples are a very small portion of actual breaches that happen. Another major concern is invasive malware and spyware which is becoming notoriously difficult to detect even with antivirus programs. Recently, it was revealed that an Instagram bug left the app vulnerable to malware attacks by hackers who could infect and gain remote access to a user’s account by simply sending them an unsafe picture via any messaging application, such as WhatsApp and email.
Experts today believe that while constant surveillance of users via microphones and cameras is not very common or feasible, users are tracked using other invasive methods. Essentially, user activity is observed down to the smallest detail, and this information is processed by near-perfect algorithms to “enhance” user experience. This same data is sold to third party advertisers, turning users into a commodity.
In 2019, two Spanish researchers also shed light on how pre-loaded apps are a big security loophole for users, making even the utmost care in privacy-related matters futile.
Thus, users are in an impossible cycle of tech dependence and privacy concerns, which can only be fixed through dedicated efforts on the part of device and app developers to secure users against external and internal vulnerabilities and breaches.

