A new Android malware has become a nightmare for over 2.5 billion Android smartphone users worldwide. The new banking malware has surfaced in the Android ecosystem, with a longer list of target apps, the ability to gain admin privileges to Android device, and the stealth to bypass a sleuth of antivirus services.
This bot was discovered by cybersecurity research firm ThreatFabric back in May, which is presumably around the time the threat emerged. Named BlackRock by its discoverers, the Android virus is based on Xerxes’ source code, a banking malware from 2019 derived from LokiBot, a malware famously known for being the base code for more strains of similar trojans.
BlackRock Android Malware: Google Update
BlackRock infects Android smartphones by posing as Google updates that ask for permission to observe one’s device actions and retrieve window content.
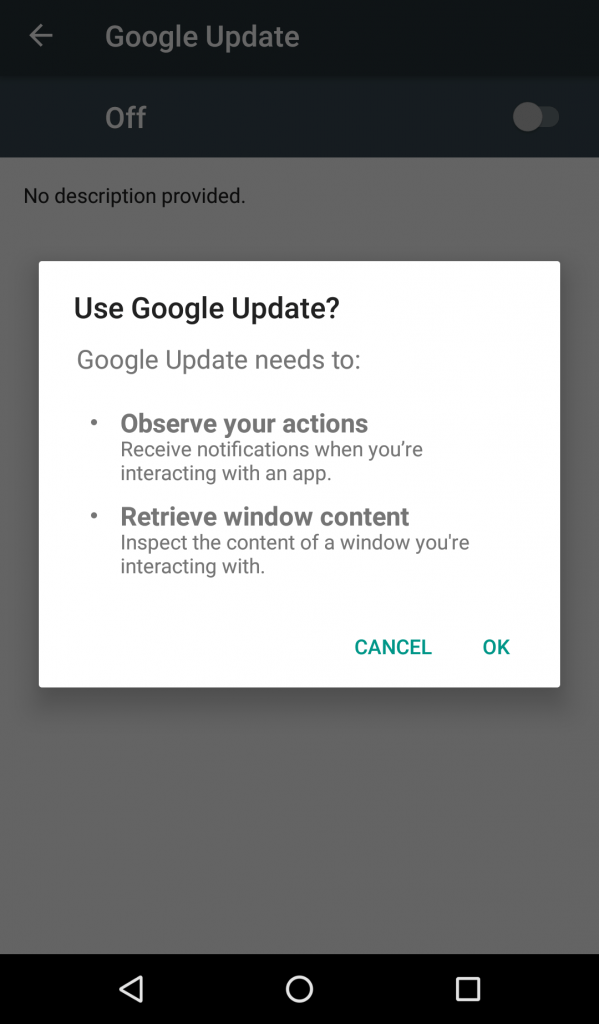
The targeted Android smartphone users do not suspect that the update alert is malware in disguise due to BlackRock’s instrument of hiding itself from the app drawer.
Once the initial permissions are acquired, the bot enables other accessibility permissions it requires by itself, such as the ability to view text messages, lock the screen, and hide notifications. After device accessibility is obtained, the software starts receiving commands from a C2 server.
BlackRock Android Malware: Banking Apps On Risk
With the various coded commands it receives, BlackRock can perform all actions relevant to the theft of banking credentials such as reading messages, sending messages, keylogging, and overlaying.
Keylogging, or keystroke logging, refers to the tracking of all the keys a user presses on their keyboard. This feature is used to steal passwords and other sensitive information such as card numbers, account numbers, and the like.
Overlaying is a feature common to many banking malwares in which the bot in question keeps running in the foreground and steals information in the form of alerts that ask for credentials for security purposes.
Apart from these standard features, BlackRock also has two features that visibly stand out.
ThreatFabric reveals infected devices get profiled by the malware, i.e., the bug gains access to the device’s work profile which then grants it the ability to control or limit the usage of certain apps and permissions. This feature is usually used by device manufacturing companies to update and control device policies. It is also used by offices to ensure work-related apps do not interfere with other apps.
The second feature that stands out is the number of apps the Android malware targets. Apart from financial apps such as payment and banking apps, BlackRock also attacks communication, lifestyle, social media, and even dating apps. Business and shopping apps are also exploited. In total, the new trojan targets 337 apps including widely used ones such as WhatsApp, Telegram, TikTok, Tinder, Grindr, Messenger, Reddit, etc. A full list of the apps can be found here. These apps are mainly spied on to access financial information.
While most banking apps are specific to America and Europe, the additional apps are global in scale. Out of the total estimated number of BlackRock attacks, the most were in Spain.

Lastly, BlackRock bypasses several anti-virus programs and device cleaners like Avast, McAfee, Kaspersky, and Superb Cleaner.
Banking Malware Seems to be on the Rise
ThreatFabric doesn’t know the scope of the harm BlackRock can inflict in the future, but a general trend for 2020 seems to be an emergence of increasingly sophisticated banking malware.
This is the third instance of a banking trojan being reported in July alone. The first came about in the second week of July, with Avast warning smartphone users against Cerberus, a bot that infects devices through apps on Google Play Store. Then, only 2 days ago, 4 Brazilian banking viruses launched worldwide.
Earlier this year, EventBot and Alien made headlines and put cybersecurity in peril.
The issue of malware is nothing new with Android. Unlike iOS, a number of issues, like fragmentation and vulnerability, has always made Android users a prime target of hackers and spammers. In May another Android malware dubbed “WolfRAT,” affected popular messaging apps, including Facebook Messenger, WhatsApp, and Line. In June 2016, more than 500 million Android devices were infected by another deadly malware.

