In the fast-paced world of cybersecurity, “zero-day” vulnerabilities loom as a formidable challenge for tech giants investing billions in enhancing user experiences. These vulnerabilities are mostly software flaws that developers fail to detect, leaving no immediate patches or fixes available to protect against potential exploitation. According to a recent report, “Google’s Threat Analysis Group,” the year 2023 witnessed a significant rise in the exploitation of zero-day vulnerabilities.
To be precise, the exploitation of zero-day vulnerabilities increased a notable 56.5% YoY, from 62 in 2022 to 97 in 2023. However, this number fell short of the record set in 2021, when 106 zero-day vulnerabilities were observed being exploited.
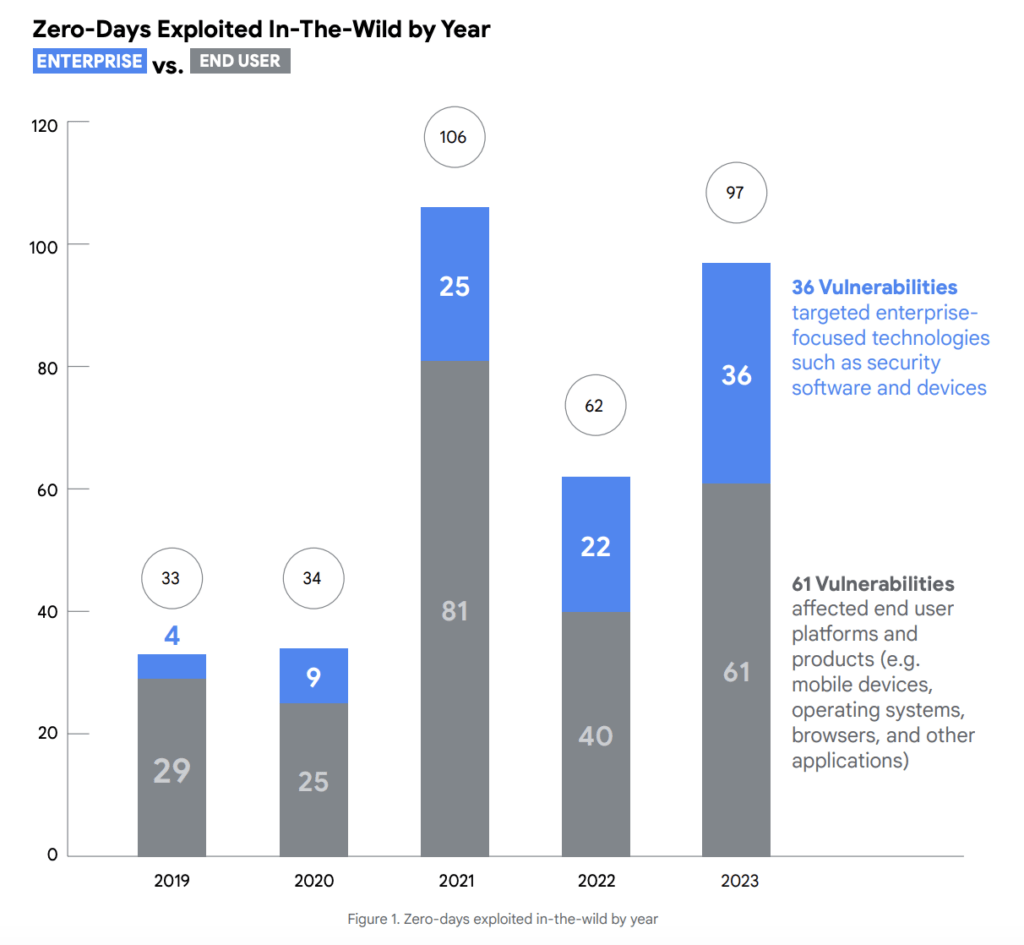
The surge in vulnerability exploitation suggests that hackers are becoming more aggressive and adept at discovering and using vulnerabilities to launch cyberattacks.
As these vulnerabilities are exploited, Commercial Surveillance Vendors (CSVs) emerge as key players in the cyber threat ecosystem. In 2023, CSVs were responsible for 75% of known zero-day exploits targeting Google products and Android ecosystem devices, comprising 13 out of 17 vulnerabilities. These CSVs specialize in selling spyware capabilities to government clients for surveillance activities.
Out of the 37 zero-day vulnerabilities exploited in browsers and mobile devices in 2023, more than 60% were attributed to Commercial Surveillance Vendors (CSVs).
Attackers have also increased their efforts to exploit vulnerabilities within third-party components and libraries. This strategy was chosen because exploiting these vulnerabilities could potentially impact multiple products simultaneously.
Threat actors across various motivations actively sought out vulnerabilities in products or components that offered broad access to multiple targets, reflecting a scalable and effective approach to launching attacks.
It is important to note that there was a whopping 64% YoY increase in the number of vulnerabilities targeted by hackers in enterprise-specific technologies during 2023. This trend was further evidenced by the widening range of enterprise vendors targeted since at least 2019, largely due to the exploitation of security software and appliances.
The People’s Republic of China (PRC) maintained its position as a leader in government-backed exploitation. PRC cyber espionage groups exploited 12 zero-day vulnerabilities in 2023, which marked an increase from seven exploits observed in 2022. This number exceeded those attributed to any other state, continuing a trend that has been ongoing for multiple years.
Payouts for Vulnerability Exploits
In response to the heightened risk posed by zero-day vulnerabilities, Crowdfense, a prominent vulnerability research hub, has been offering substantial rewards to skilled hackers over the past few years. The bug bounty program, initially announced at $10 million in 2019, has now increased to $30 million this year.
Hackers are encouraged to identify previously undiscovered vulnerabilities in various platforms and products, including Android devices, popular browsers like Chrome and Safari, and messaging apps such as WhatsApp and iMessage. This initiative aims to incentivize researchers to uncover critical vulnerabilities in widely-used technologies, thereby enhancing cybersecurity and protecting users’ data.
Interestingly, the payouts for successful submissions vary based on the nature and impact of the vulnerability discovered. For instance, Crowdfense is offering the highest rewards for iPhone exploits.
- Zero-click exploit targeting SMS/MMS functionality on a device: from $7 million to $9 million
- Zero-click exploit targeting iOS devices: From $5 million to $7 million
- Zero-click exploit targeting Android devices: $5 million
- Zero-click exploit targeting both WhatsApp and iMessage: from $3 to $5 million
- Zero-click exploit targeting the Chrome browser (RCE + SBX + LPE): $1.5 million
- Zero-click exploit targeting the Safari browser (RCE + SBX + LPE): $500,000
- Zero-click exploit targeting the Microsoft Windows operating system(RCE + LPE): $2 million
Government security agencies often require sophisticated hacking tools to track and investigate criminal activities or threats posed by malicious actors. As a result, companies like Crowdfense sell exploits, including zero-day vulnerabilities, to various organizations, including government agencies. These proactive efforts are essential for safeguarding sensitive data, protecting systems from cyber threats, and maintaining the integrity of digital environments within an ever-evolving threat landscape.

