After minting million from internet and mobile ad frauds now scammers have resorted to Smart TV ad frauds.
Smart TV advertisers had to recently lose a lot of ad dollars because of a humongous scam operation that has been set in motion for the past few months!
In a recent discovery, the cybersecurity firm and bot detection platform White Ops found out about a huge online fraud operation which was running for a past few months. This operation has been impersonating Smart TV users which in turn kept returning bogus impression numbers to online advertisers who have been running ads all this time. They also managed to eat into the ad profits which were supposed to originally go to the online publishers.
This operation has been named as ‘ICEBUCKET’ as of now and has also been reportedly described as one of the largest cases which involve SSAI aka Server-side ad insertion spoofing known to date.
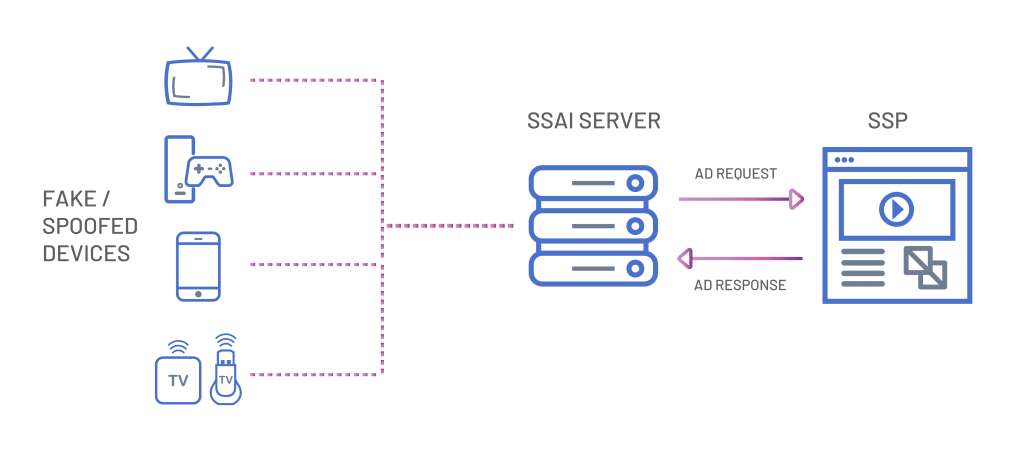
SSAI servers essentially work as an intermediary between an ad platform and the end-user. The way SSAI servers work is by sending all the ads to apps running on a consumer’s devices. Now, these devices can be anything from smart TVs, computers, smartphones to tablets and so on.
The reason online advertisers prefer to use SSAI servers and are so very popular today is that they allow the complete control of ads being shown on a consumer’s device in real-time without hindering an app’s code.
It is now being considered by the White Ops Team that the people behind the entire operation of ICEBUCKET has probably come across a weakness or vulnerability in the mechanism of SSAI server communications.
It is by exploiting this same weakness the ICEBUCKET group for the past few months has been connecting to SSAI servers and requesting ads to be shown on non-existing devices.
The ICEBUCKET team, in some cases, has also been mixing organic and their fake traffic. This the White Ops speculate could be for two reasons. One, it could be to make it more difficult for its operation to be identified. Second could be the fact that their operation is some sort of a ‘fraud-as-a-service’ option.
As for the reason of targeting their efforts mostly on spoofing smart TVs and other connected TV devices, it is because of the fact that the CPMs (aka cost per 1000 impressions) rates for ads being displayed on these devices are much higher than the others.
The White Ops Team observed that the ICEBUCKET group has been spoofing CTV aka connected TVs such as Roku, Samsung Tizen, GoogleTV and other Android-based streaming devices
They also reportedly mentioned that this online group of fraudsters spoofed a whopping 1,000 different types of devices or user-agents by using more than 2 million IP addressed located across 30 different countries. However, the White Ops team mentioned that most of the bad traffic seemed to come from smart TVs in the US.
According to Statista, as of 2019, there existed 102.6 million smart TV users which are projected to grow to 119 million users by the year 2022. This shows that the scope of the damage that can be done via bad traffic coming only from the United States alone could be devastating for online advertisers.
In January at its peak, this malicious operation was able to generate close to 1.9 billion ad requests to SSAI servers per day. The scale of the operation was uncovered when it was found out that almost two-thirds of the CTV SSAI ad traffic in the month of January this year came only from the ICEBUCKET crew set up non-existing devices.
The ICEBUCKET group used more than 300 app identifiers to request the ad traffic on behalf of non-existential devices which is huge. These app IDS are the apps and financial mechanisms which allowed this group to collect the ad profits which were supposed to go to the legitimate apps instead.
Lastly, the White Ops team of security experts believe that fraudulent campaigns such as these might just start popping up in more numbers. This is mainly because the vulnerability that is being leveraged to run this scam still hasn’t been identified. We will keep you posted on all future developments.

