Looking to protect your business from cyber-attacks?
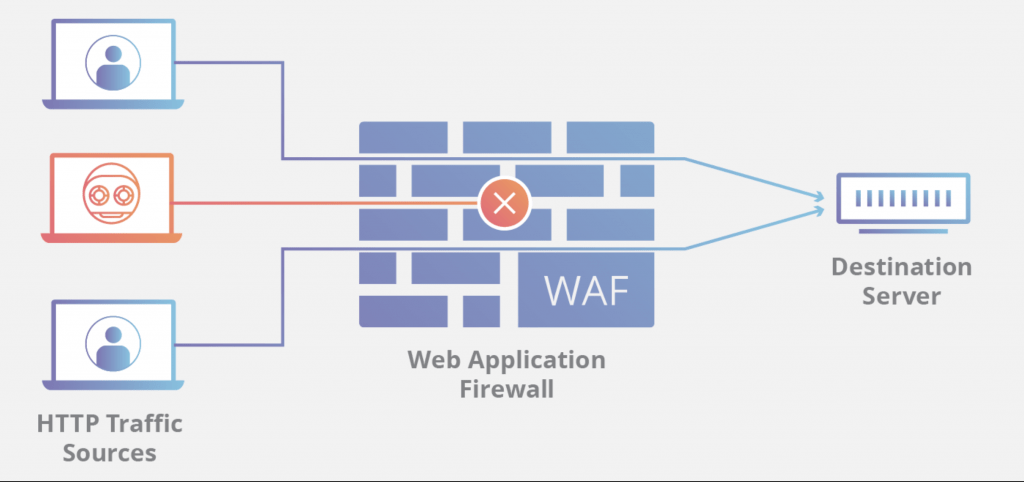
A key way to prevent attacks is by using a web application firewall (WAF), which analyzes and inspects incoming traffic and blocks nefarious actors from infiltrating your system.
Read this complete guide to learn more about the different types of web application firewalls and how to choose the right WAF for your business.
What is a web application firewall?
A web application firewall, also known as a WAF, protects web applications by monitoring web traffic between a web application and the Internet. It’s one part of a holistic cybersecurity defence system.
WAFs filter out malicious traffic based on a set of policies that dictate which kinds of traffic can or can’t pass through the barrier. In doing so, they prevent attacks such as cross-site scripting, file inclusion, SQL injection, and more.
What are the different types of WAFs?
WAFs can either be cloud-based or hardware-based.
Cloud WAFs are managed through a cloud vendor and are accessed through a web platform or mobile app. Cloud WAFs tend to be the preferred type of firewall since they’re easier to implement and maintain, don’t require additional physical resources, and have a higher computing capacity.
In contrast, hardware WAFs are implemented on-premises and require the procurement and instalment of hardware or software. Hardware WAFs typically need to be managed by a dedicated in-house team, as they require consistent maintenance and updates and may need to be scaled depending on traffic capacity.
How does WAF work?
A web application firewall can operate on either a negative security model or a positive security model.
Negative models are based on blacklists. Blacklisting models work by specifying the types of traffic that will be prevented from passing through the WAF. As traffic enters the firewall, the specified types of traffic are blocked.
Positive security models, on the other hand, are based on whitelists. Whitelisting models only allow specified web traffic to pass through, blocking all other traffic.
The final WAF security model–the mixed or hybrid model–works by taking the best of both worlds. This model combines both whitelisting and blacklisting, specifying which types of traffic should be let through and which types of traffic should be blocked. Hybrid security models are often the most effective choice for web applications on both the public internet and on internal networks.
What to look for in a web application firewall
To choose the most effective WAF for your business, keep an eye out for the following important features:
l Cloud and on-premise security – A good WAF protects applications both on-premises and in the cloud. All applications, regardless of their location, should have a unified management system with the same security policies.
l Flexible deployment options – Choose a WAF that you can deploy on-premises or integrate within the cloud.
l Protection against top threats – The most powerful WAFs should be continuously updated with the latest threat data and protect against OWASP Top 10 and Automated Top 20 threats. These threats include cross-site scripting, file inclusion, SQL injection, illegal resource access, and more.
l Accurate attack detection – Choose a WAF that effectively blocks all bad traffic while letting good traffic through. Aim to quickly and accurately detect attacks while minimizing false positives.
l In-depth reporting – A strong WAF should be accompanied by in-depth reporting and an intuitive, easy-to-use analytics dashboard. This will help you assess your security status, keep an eye on threats, and meet regulatory compliance standards.
l SIEM integration – Be sure your WAF integrates with your Security Information and Event Management (SIEM) systems so that you can keep your data organized and all in one place.
Choosing a WAF for your business
Every business needs a web application firewall as a core component of a more holistic cybersecurity strategy. WAFs can either be implemented in hardware or installed via the Cloud. When it comes to your security model, a hybrid of blacklisting and whitelisting security models tends to be most effective.
Finally, you should choose a WAF that detects threats with accuracy and precision, integrates flexibly within your existing hardware or software infrastructure, and displays comprehensive threat analytics on a single intuitive dashboard. This way, you’ll be able to successfully protect your business and keep your data safe.

