While the godawful data breach scandal by Social-media giant Facebook still brews fresh, resulting in a loss of million dollars, other tech-firms are also in balls-and-chain when it comes to user privacy.
Right of the press report by Wall Street Journal claims that Google has allowed third-party app developers to delve into emails of Gmail users. The Wall Street Journal, which was the first to point this “tech’s dirty secret” has been hiding in the invisibility cloak for a long time now. Undermining the whole fiasco leads to the upshot of Gmail’s access settings which allows specific software developers to sift through user’s emails and retrieve recipient addresses, timestamps and if it’s less than a nightmare, even entire message.
The third-party developers then share the user details with marketers, and strip in funds, in return. Considering Gmail’s huge user base that spans across 1.4 billion users, this is a vast pool of private data, out in the open for sale.
In the reports, Wall Street Journal has kept eagle-eyes on two third-party apps.
One is Return Path, an app which is responsible for collecting data for marketers from under’s mailbox. For its own beneficial purpose, this company has sifted through over 8,000 emails in a span of two years.
An able partner-in-crime of Return Path is an email management app, Edison Software. It is allegedly allowing its employees to access user emails to facilitate app’s Smart Reply feature.
A Run-down Along Gmail Route
The hugely successful Google email client, Gmail, has been garnering additional functionalities from innumerable third-party developers.
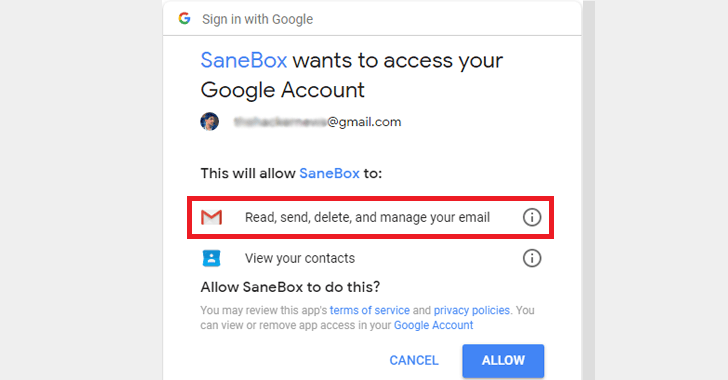
First, one must build an app that connects to Gmail using the Application Programming Interface (API) supplied by Google and the successive events are a cake-walk. These apps provide additional functionality to the Gmail, for instance, to quickly unsubscribe from any marketing emails sent to your address.
Herein, Gmail, carefully and tactfully, nudges users into granting third-party access. When Gmail users sign-up for any services, Google requires them to grant permission. However, once users grant permission, this app can browse through their mailbox and can read the contents of sent and received messages.
As of now, Google has not disclosed the number of apps currently having access to Gmail.
However, as a good deal of waving past the allegations, developers claim that this practice is not illegal and user agreements envelop the same under its guidelines. Sifting through users’ emails stands useful for companies to keep track of user’s shopping habits or other “relevant” trends, deemed necessary.
Crossing the Privacy Boundaries
Given the above argument, one might draw a conclusion that email providers, facilitating third-party developer’s access to scrawl through user’s private emails are common, and hence banal practice to be worried about. However, the catch here is that although Google continues accessing user mails, it goes out of boundary by allowing other companies to do that.
While there’s no evidence that Gmail add-on developers have misused any data, as of now, one can surely grasp how discourteous it is to breach user privacy and dig into private emails. Again, there have been incidents surfacing up now and then, which clearly depicts the vulnerable states of certain tech-giants when it comes to data privacy and security issues. With the fiasco wherein Google users fell victim to a phishing attack, this outlines how crucial it is to realize the depth of issues. Certain doppelganger that disguised itself as a permissions request from Google Docs tried to gain access to user contacts, replicating Google’s authorization system. This attack highlights the weakness of Google’s permissions system.
As part of the new updates, Google introduced a new search functionality that allows them to customize additional settings as well as tiny tutorials, like for changing the password.