Cyber attack is a potential threat to every internet user. The technology that facilitates connectivity on-the-go, also makes it easy for hackers to infringe data security. A recent demonstration by a group of researchers from the Shanghai Jiao Tong University, the University of South Florida, and the University of Massachusetts at Boston, revealed a new technique that can reveal private information through analyzed radio signal interference using a rogue Wi-Fi hotspot. In a highly advanced manner, a user’s finger movements on a touchscreen phone or a computer’s keyboard are sniffed by the Dubbed Windtalker attack by reading the radio signal patterns called Channel State Information (CSI).
Windtalker Attack is Highly Advanced
While entering any PIN or password or swiping the unlock pattern, finger movement alters the Wi-Fi signal transmitted by the phone, and these movements are imprinted into the signal. When the device is connected to a public Wi-Fi which is controlled by a hacker, they intercept, analyze and reverse engineer these signals to guess the data that was previously entered. The catch here is, this guess work is mostly correct. It doesn’t even require access to the victim’s phone which makes it much more convenient. However, the Windtalker attack works only on a router with multiple antennas that use the Multiple Input Multiple Output (MIMO) technology. MIMO technology allows the router to connect and transmit data from multiple devices simultaneously.
Windtalker Attack Accuracy is Something to Worry About
According to the tests carried out by the researchers in the real world scenario, the accuracy of this attack technique turned out to be 68% accurate. However, the accuracy is different on different mobile phones. The accuracy increases with the user who types more. This helps the attacker in collecting more data. The attacker dupe in the users by providing free Wi-Fi access and in return the user has to finish the online training by clicking the designated numbers. Moreover, they can also mimic text captchas to make the user enter the designated numbers.
Data Breaching is Only Increasing with Technological Advancements
Data breaching is increasing rapidly with advancement in technology. In the first half of 2016, there were 974 publicly disclosed data breaches which led to theft or loss of 554 million data records. It is a 31% increase from 424 million data records which was compromised in the previous six months. Moreover, 52% of the data breaches in H1 2016 couldn’t identify the exact number of data that were compromised. It means that the number might increase significantly from 554 million for H1 2016 when more information about the breach is disclosed or made available. This number can be broken down further in the following manner:
- 35 records per second
- 2,116 records per minute
- 126,936 records per hour
- 3,046,456 records per day
Attackers are interested in the data as they tend to exploit them for their benefits or trade the data in the dark web against some money. The amount of money depends on the importance of the data. Out of the total 974 breaches, Identity theft attacks alone accounted for 621 incidents (64%) and theft of 294 million data in the first half of 2016. But the most surprising fact is these attacks have increased a huge 38% during the previous six months (H2 2015). The other types of incidents reported were financial access (16%), account access (11%), Existential data (5%) and nuisance (4%). This kind of theft can be used to create fake documents, send messages or emails from the stolen identity, or using it for other wrong purposes.
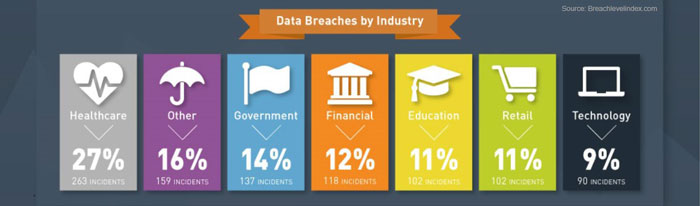
Based on the industry type, healthcare industry was the most affected with about 263 incidents (27%) of data breaches followed by other (16%), government (14%) and financial industry (12%).
Keep Your Data Secure
Several companies, as well as the government, has been working to keep these attacks under control. However, the attackers are always successful in finding out different ways to breach. Companies and government use a three-step approach to keep the data secure. The steps are as follows:
- Encrypt the data: All the sensible data whether in physical networks, virtualized environment, the cloud, or in motion, should be encrypted to protect vital information.
- Store and Manage Keys: Encryption requires crypto management platform. So, the key should be stored in a vault away from the encrypted data, and a process should be implemented to limit access and reissue of the key.
- Control User Access: Strong authentication of the user through a verification process should be implemented, and user access level should be defined to manage user access.
However, safety largely remains in the hands of the users. The user should be careful about their behaviour while browsing the web. The users should follow the usage guidelines. They should try to avoid connecting to unknown public Wi-Fi networks and clicking on unknown links, emails, and messages.
Technology is advancing, and consumers are becoming more and more dependent on the digital world. The chances of becoming victim to cyber-attacks have also increased manifold times. Hence, Internet and Network users should be very careful. After all, prevention is better than cure!