Google’s ‘bounty hunter’ program known as Android Reward program has rewarded 82 researchers who have successfully pointed out the Android Vulnerabilities. The company has rewarded them with a whopping $550,000 at an average of $6,700 per researcher. ‘More than a third’ of the 250 ‘qualifying’ reports that Google received were related to Media Server and in turn, Google has made Android OS more secure to vulnerabilities especially for its upcoming Android N.
Google launched this open Security reward program in 2010 and expanded this program to Android platform on June 16, 2015. The company has given up to $38,000 per report that Google made use of to protect users from vulnerabilities by fixing them. While the prime aim, according to the company, is to improve Android security and the targeted devices are Google’s own Nexus Devices, more than a quarter of issues were reported in code that is developed and used mainly outside of the ‘Android Open Source Project’.
The most benefited one from the program, Peter Pi @heisecode, won $75,750 for his 26 vulnerability reports whereas 15 other researchers received more than $10,000 each. Although the topmost prize for the complete remote exploit chain leading to TrustZone or Verified Boot compromise remained unclaimed.
Since the launch of the program, the extravagant Google has awarded a whopping $1.5 million to its researchers who have successfully pointed out the vulnerabilities in its Chrome and Google products.
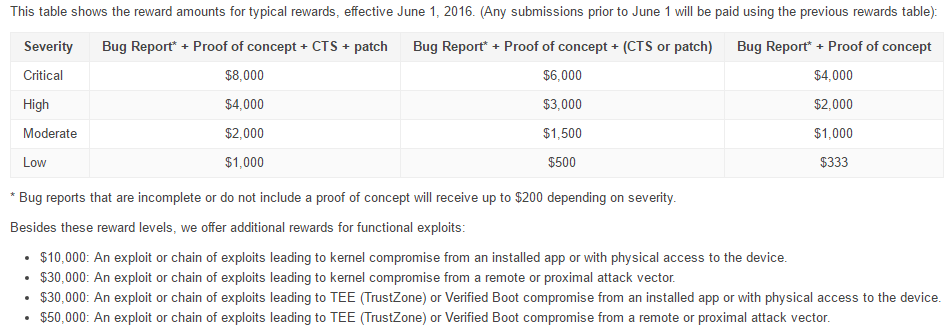
The search giant seemed to be impressed by the work, has decided to increase the reward prize from June 1, 2016. For a ‘high-quality vulnerability report with proof of concept’, the company will shell out 33% more reward. The additional CTS Test, or a Patch along with the ‘high-quality vulnerability report’ will garner 50% increase in reward. Whereas ‘A remote exploit chain or exploits leading to TrustZone or Verified Boot compromise’ has a considerable increase in reward from $30,000 to $50,000. The one’s who are interested in can learn how to make a high-quality report can visit Bug Hunter University.
Android Vulnerability: A Big Challenge for Google
Android empowers 84.1% of the total smartphones in the world and thus is the main targeted OS for the hackers. The OS empowers 1.4 billion active users worldwide and had recorded 65 billion app downloads last year.
Bugs are everywhere even in the most secure platforms like Mac OS and iOS. The iOS on iPhone is identified as second most vulnerable software with 375 vulnerabilities, whereas Android sits at 20th position with 130 vulnerabilities in 2015.
The numbers speak for themselves and thus Android is bombarded with bugs and vulnerabilities every now and then. According to the latest report, a vulnerability named Accessibility Clickjacking affected 500 million of smartphones running on older version of Android OS.
The reward program is targeted only at Google’s own Nexus devices as they are regarded as pure Android devices. In contrast, other manufacturers modify Android platforms before they push to devices. This has caused a big challenge for Google in a form OS Android Fragmentation from the beginning. Android Smartphone OEMs modify the OS in an attempt to provide a unique experience to their users.
The Android behemoth has invested heavily in Android SDK to provide a safe and secure environment to its developers which accidently may inject malicious code in their apps. On the other hand, Google Play services try to intercept attacks on Android platform. Following the Google’s methods of securing its Nexus devices, major OEM’s have also started releasing security patches to remove any vulnerabilities from their devices.
According to a report, Google has been able to secure 1 billion devices by running daily scans through Play services on over 400 million devices, thus, removed 100,000 apps that possessed major vulnerabilities from the Play Store.
Google has apparently left no stone unturned to uproot the vulnerabilities and thus its next version Android N seems to be quite secure. Learning from his previous mistakes, Google has integrated default encryption in Android Marshmallow thus taking security measures to a next level.