Cloud computing has become a data-haven today. Owing to its easy accessibility and reduced cost, it is one of the widely used means to store data in most of the IT firms. Cloud computing, though, depends completely on Internet connectivity, Internet design, unfortunately, does not have the high levels of expected security.
Distributed Denial of Service attack, widely known as DDoS attack, is the primary threat to cloud computing. The DDoS attacks attempt to make the online data unavailable by redirecting overwhelming traffic, from multiple resources. The trend of the attacks is changing across quarters. In Q2 2015, the attack, though less powerful, lasted longer, as stated in The State of the Internet – Security Report by Akamai.
DDOS attacks witnessed an increase of 132.43% in Q2 2015 compared to the second quarter last year, with China being the top source of the attack, accounting for 37.01%, followed by the US and the UK. China is the biggest perpetrator as well as the target of these attacks. Brazil emerged as the new hub of hackers accounting to 11% of all attacks.
Interestingly, from another report by Incapsula, the longest attack ever reported in this quarter, was for sixty-four days.
The Akamai report, on the other hand, claims that the largest DDoS attack happened at 240 gigabits per second, which continued for more than 13 hours. However, the peak bandwidth attack existed only for around two hours.
The Q2 report by Akamai claims the Gaming Sector to be the worst hit, with more than 35% of attacks faced by it. The sector is followed by Software and Technology at 28%, and Internet and telecom at 13%. Besides, from the financial services, Banks and trading platforms accounting for 8% of attacks and see few larger attacks of 100+Gbps of the quarter. Most of the individual customer attacks in the financial services industry are found to be Shellshock attacks. However, an article at TCS website claims Banking industry is the main victim of attacks, struggling to counter them. Devising a strategy though may not be an easy job, as no two DDoS attacks are alike.
The report also focuses on common nine web application attack vectors. The new types of attacks are cross-site scripting (XSS) and Shellshock. The older attacks include JVMi, SYN, SSDP, SQLi and LFI. SQLi, which is up by 75% from the last quarter and accounts for 26% of all attacks. On the other hand, LFI (Local file infusion) attack dropped significantly to only 18%in the second quarter.
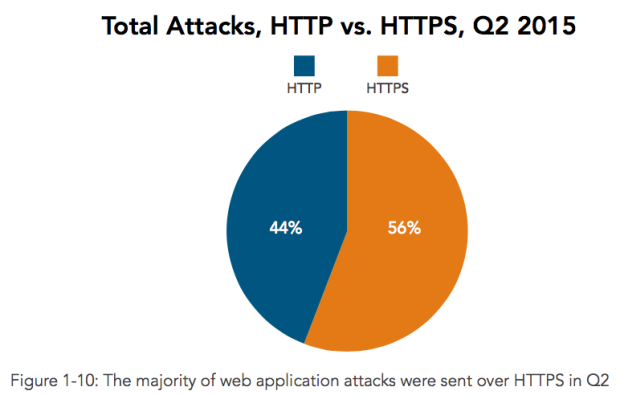
Surprisingly, HTTPS enabled sites, where data is transmitted over a secured connection in an encrypted mode, have been the target of 56% of the total attacks as compares to 44% of attacks on the HTTP (non-secured connection) sites, report reveals. This is really surprising considering the fact that most of websites, which are offering transactional services are highly targeted by hackers. Thus, HTTPS can not be considered as secure as it was originally thought.
Though the Q1 report of Akamai on Internet security pointed to third-party plugins to be the malicious actors and explained the same, the Q2 report has taken the widely used data exchange platform WordPress for a case study. The Q2 report reveals 49 prior unknown vulnerabilities due to the third-party WordPress plugins. The report also recommended that site owners must research the plugins prior to utilizing and to ensure the security of the plugin.
The Tor project ensures the anonymity of the website users, that employs an onion routing method, with a separate entry and exit nodes. The onion routing makes it easy to peep through the network and attack the websites. The Retail industry remains to be the most targetted victim of Tor attacks. Financial services and high technology follow the retail industry in terms of the number of attacks from Tor.
A glimpse into future of internet security
The rising internet security threats pose a new challenge. It is vital to acquire unparalleled data in regard to the security features of the web application used. Additionally, effective engagement of software and hardware is a prior requirement. From the findings of Akamai report, it is evident SYN and SSDP vector attacks are the most threatening ones. Here are few takeaways to keep your network safe.
- Home-based networks being the favorite target of attacks to keep away these networks from the attacks it is necessary to employ a properly configured home firewall.
- Universal Plug and Play (UPnP) devices connected to home networks are vulnerable to the attacks. The home user can always disable the UPnP devices on the router and the other devices facing the public that do not require the router connection.
- In case of device manufacturers, it is required to push the firmware of the UPnP device complementing to the LAN network it is used.