It’s a no-brainer; website downtimes have to be prevented to avoid losses, not just in terms of revenues but also to avoid disappointing or irritating current and potential customers. That’s why it’s very important to maintain a highly-available infrastructure and to incorporate quick response mechanisms to possible online threats.
In building such an infrastructure, an enterprise has the option to train and maintain their own departments to specifically handle threats. However, it is also a good idea to employ the services of third-party solutions providers as a more cost-effective and efficient alternative. For either option, the key point is to ensure the reliability of your infrastructure, whether against high demand or actual malicious attacks.
Be proactive in ensuring high availability
Whether you are running a customer-facing infrastructure or if you are running an enterprise system used internally, adequate uptime is necessary to ensure service-level agreements (SLAs) are met. High Availability requires a 99.999% uptime. Running a highly available infrastructure involves ensuring consistent monitoring, in order to be proactive in ensuring that your service delivery is top-notch. You will also need to incorporate load balancing mechanisms to efficiently distribute load across different servers. A proper failover mechanism is needed to ensure that no single point of failure can cause your entire service to go offline.
Preparation is key
Preparation against malicious attacks involves a number of actions aimed at setting up the necessary defenses and courses of action to address an online threat. This includes the installation of all necessary software protection and the proper training of the person or group of personnel who will be responsible for handling threats as they emerge.
The following pointers should be taken into consideration when doing the necessary preparations to be able to rapidly respond to threats to avoid site downtimes and revenue losses.
Monitoring should be round the clock
There should be continuous uptime monitoring, as well as site health tracking or website error detection. Moreover, it’s always preferable to have real-time alerts for the convenience of automatically informing the parties or departments that should be immediately updated whenever threats are detected. Fortunately, many online security solutions already provide these monitoring features even on their basic/personal packages.
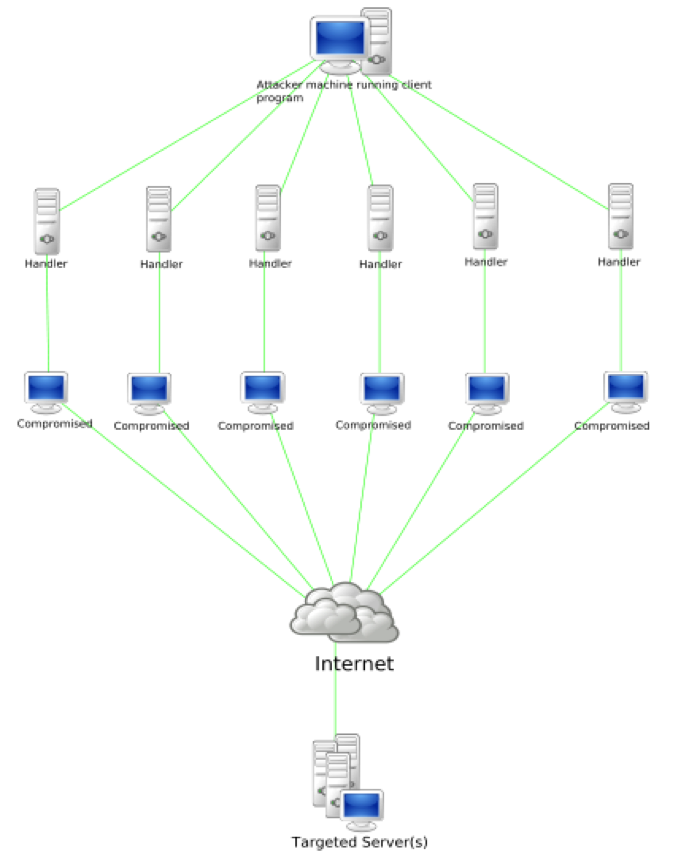
Ensure protection from DDoS, spam, abuse, and other related threats
For enterprises, it is very important to maintain protection from the following typical threats: Distributed Denial of Service (DDoS) in both network and application levels, spam and abuse, SQL injection, XSS or cross site scripting, screen scraping, and brute-force password cracking. It always helps having rule-based and reputation firewalls along with other solutions designed to prevent the aforementioned attacks.
Use speed-enhancing solutions
In addition to the use of SSL and load balancing, it is also advisable to employ content caching, cache rules and purge, and traffic optimization functions to make sure that sites are running at their optimum speeds. If your site runs at a certain performance level, you can instinctively notice slowdowns that can be indicative of malware infections or other forms of attacks.
When a problem is already taking place
Of course, even the best preparations cannot guarantee that a threat will not be able to get through. It’s also important to know what to do if ever a problem is already starting to affect the enterprise’s resources. The following should serve as guides on what ought to be done.
Carefully examine the problem and focus on the relevant details
There are advanced data collection and visualization tools that can be used to thoroughly evaluate the problem and come up with suitable solutions. The goal in prudently studying data is to make reaction time faster, to address the problem before it eaves a major impact or an irreversible consequence.
Minimize or mitigate the impact of an attack
The impact of an attack can be minimized if acted on early. In the case of DDoS, for example, blackholing and sinkholing can be employed to route traffic and clean it by filtering bad packets. Traffic may also be made to pass through a cleaning or “scrubbing” center using methods such as proxies, tunnels, or direct circuits.
React in real time
Internet security threat management should be a proactive process. Actions to mitigate the effects of an attack should be promptly undertaken as based on what is happening on the network or the sites being affected by an attack. Reaction time should even be accelerated. Generally, dealing with an already developing attack would appear to be almost too late for site or network administrators. Preparations to prevent attacks should have been done beforehand.
It’s never good to be simply reactive, or to deal with the problem when it already exists. However, this does not mean that all is lost once an attack manages to get through. Using reliable tools for extracting network threat statistics and by getting updated with the latest information on attacks and the corresponding solutions, mitigating measures can still be done.
In sum, it can be said that to be able to rapidly respond to online threats, both prevention and rectification measures are necessary. Preparing is not going to enough. It’s not right to assume that preparations can guarantee that threats won’t succeed in causing any harm. The worst case scenario should always be taken into account. Moreover, it helps having access to reliable protection and mitigation solutions especially when you don’t have solid know-how and experience in warding off and resolving problems caused by various forms of online attacks. If you think training an IT specialist to deal with all possible threats is not that viable, there’s always the option to avail of the services of third party online security solution providers.